Let us Hack
you firstLet us Hack you first
No more waiting for availability and overpriced quotes. AISafe can help you secure your Web Application any time of the day.
Join the Waitlist
Be the first to know when we launch.
Products & Solutions
Source Code Audit
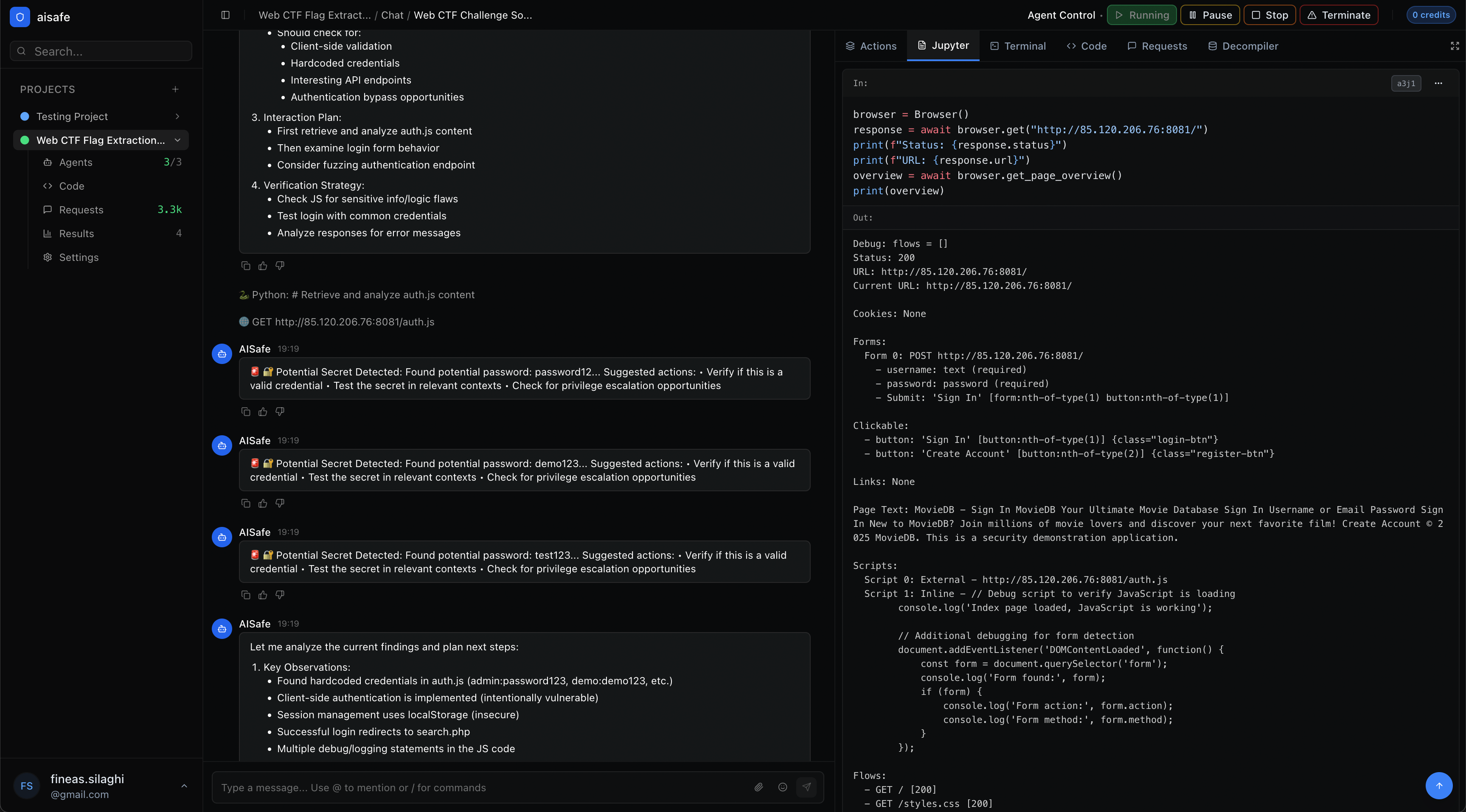
Source Code Audit
In an era where AI generates massive amounts of code, the only way to secure it at scale is with AI. You define the scope and we deliver reviews that typically take days, in hours, with complete coverage.
MVP DemoBlack-Box Pentest

Black-Box Pentest
No more waiting for vendor capacity or resource availability. We offer on-demand pentesting by autonomous AI agents, that think like elite hackers and hack at machine speed, for any web application, endpoint, or feature.
Join the WaitlistVerified Reports

Verified Reports
Turn your security audits into trust signals by allowing us to host your verified report for one year, making it shareable via a password-protected link with anyone you choose - investors, customers, or compliance teams. Annual renewal ensures your security posture stays current.
Learn More
Source Code Audit
In an era where AI generates massive amounts of code, the only way to secure it at scale is with AI. You define the scope and we deliver reviews that typically take days, in hours, with complete coverage.
MVP Demo
Black-Box Pentest
No more waiting for vendor capacity or resource availability. We offer on-demand pentesting by autonomous AI agents, that think like elite hackers and hack at machine speed, for any web application, endpoint, or feature.
Join the Waitlist
Verified Reports
Turn your security audits into trust signals by allowing us to host your verified report for one year, making it shareable via a password-protected link with anyone you choose - investors, customers, or compliance teams. Annual renewal ensures your security posture stays current.
Learn MoreHow AISafe works
One network of security agents to secure them all, depending on each project's individual needs.
Source Code Audit
An army of specialized agents that don't just report issues - they understand your codebase and perform a deep semantic analysis that pinpoints the findings to the exact line of code, while delivering ready-to-apply remediations.
Black-Box Pentest
Like running a bug bounty program where the hackers never sleep and every report is gold. No duplicates, no false positives - every finding comes with a working proof-of-concept, safely validated against your staging environment.
For Security Experts
Interactive mode exists to offer security experts the ability to conduct arbitrary investigations / experiments, alongside the ones performed autonomously by the agents
Source Code Audit
An army of specialized agents that don't just report issues - they understand your codebase and perform a deep semantic analysis that pinpoints the findings to the exact line of code, while delivering ready-to-apply remediations.
Source Code Audit
An army of specialized agents that don't just report issues - they understand your codebase and perform a deep semantic analysis that pinpoints the findings to the exact line of code, while delivering ready-to-apply remediations.
For Developers
Fully autonomous mode was designed specifically for developers without extensive security background
Black-Box Pentest
Like running a bug bounty program where the hackers never sleep and every report is gold. No duplicates, no false positives - every finding comes with a working proof-of-concept, safely validated against your staging environment.
Black-Box Pentest
Like running a bug bounty program where the hackers never sleep and every report is gold. No duplicates, no false positives - every finding comes with a working proof-of-concept, safely validated against your staging environment.
AISafe in Action
Real results with meaningful impact. See what your Friendly Neighborhood Hacker achieved in the wild.
CTF Competition Track Record
Bug Bounty Programs
Public Benchmark Performance
Web Application
[REDACTED] *************************************************** *************************************************** *************************************************** - full details will be published post-mitigation.
Web Framework
[REDACTED] *************************************************** *************************************************** *************************************************** - full details will be published post-mitigation.
Pricing
Simple token-based pricing. Pay only for what you use.
Security Review
50 tokens/hour
The number of hours is determined based on codebase size or fixed 48h for Black-Box Pentest
- Realtime streaming of findings
- Automated reports
- Real-time alerts
- Actionable remediation suggestions
- Detailed proof-of-contept exploits
Enterprise
Talk to us
For teams who require Continuous access to the AISafe platform.
- Unlimited tokens
- Multiple Accounts
- Dedicated support team
- Realtime streaming of findings
- Actionable remediation suggestions
- Detailed proof-of-contept exploits
Ready to secure
your app?
Join the waitlist today and be the first to experience the next generation of AI-powered security engineering.



